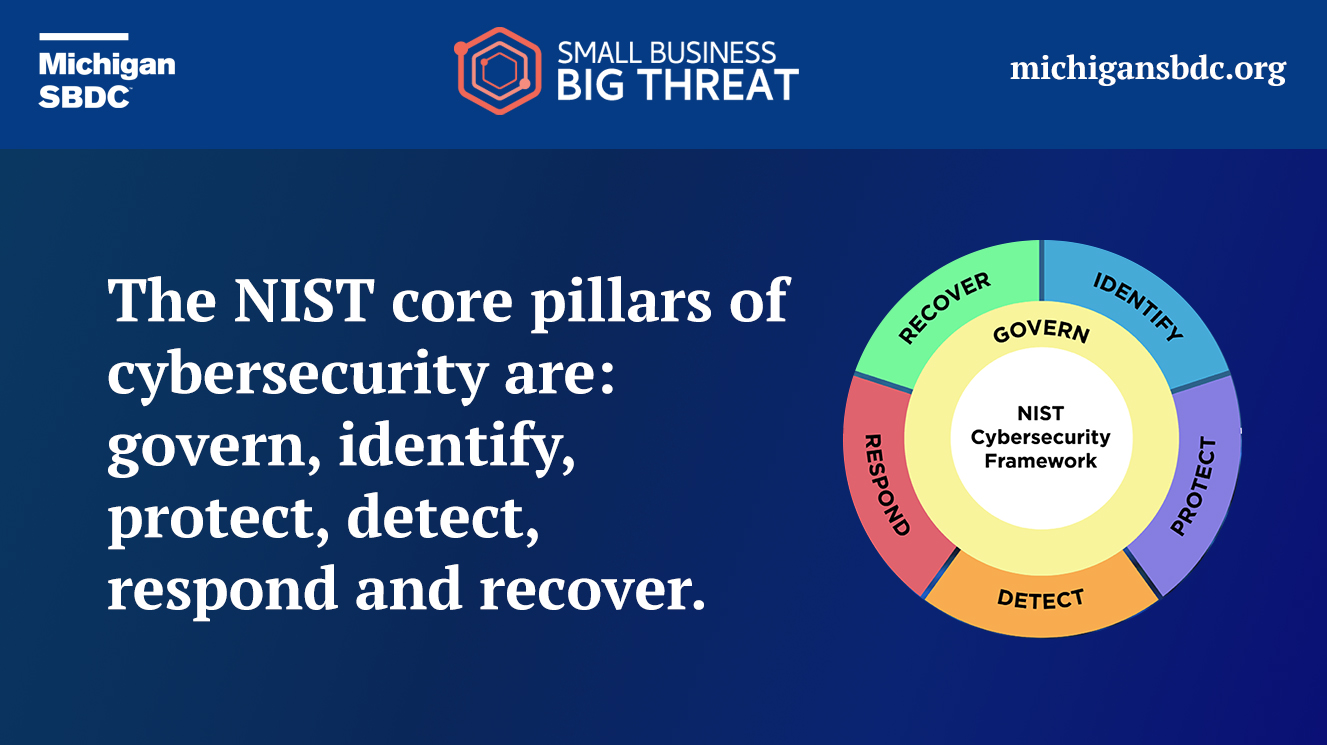
 Last week we wrote about the CIA Triad (Confidentiality, Integrity, and Availability) as being at the center of cybersecurity, this week will be about the core pillars of cybersecurity. For our blog entry, we will be utilizing the NIST Cybersecurity Framework 2.0 to establish our core pillars of cybersecurity. These core pillars are: Govern, Identify, Protect, Detect, Respond, and Recover. NIST describes these as the core Functions of cybersecurity.
Last week we wrote about the CIA Triad (Confidentiality, Integrity, and Availability) as being at the center of cybersecurity, this week will be about the core pillars of cybersecurity. For our blog entry, we will be utilizing the NIST Cybersecurity Framework 2.0 to establish our core pillars of cybersecurity. These core pillars are: Govern, Identify, Protect, Detect, Respond, and Recover. NIST describes these as the core Functions of cybersecurity.
Why core functions
When building a cybersecurity program to protect a small business, having a standard framework is important. The framework will be what helps guide a small business in protecting itself from cybersecurity risks and threats. The core functions provided by NIST offer the ability to organize for the cybersecurity program outcomes “at their highest level.” NIST describes these as:
- Govern: The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.
- Identify: The organization’s current cybersecurity risks are understood.
- Protect: Safeguards to manage the organization’s cybersecurity risks are used.
- Detect: Possible cybersecurity attacks and compromises are found and analyzed.
- Respond: Actions regarding a detected cybersecurity incident are taken.
- Recover: Assets and operations affected by a cybersecurity incident are restored.
Each is important
These six pillars all play an important function in protecting a small business from cyberthreats. Let’s add some depth now.
- Govern: The heart of the cybersecurity program, this states the why, how, who, what, and so on of how the small business wants to protect itself. This also includes knowing any legal or statutory requirements depending on its industry.
- Identify: Before you can start protecting your assets, the business needs to know what they all are. This includes all devices both on and off the business network, the business data and especially the business critical data, and all solutions in which its employees will interact like online cloud platforms.
- Protect: As its namesake says, this is how the business will protect itself after identifying all of its assets. Whether it is utilizing password managers, multifactor authentication, endpoint protection, and so on.
- Detect: While the business is protecting itself, sometimes cybercriminals still find a way in. This pillar establishes how a business will detect and analyze possible cybersecurity incidents. This could be manually viewing logs and employees reporting issues or by having a combination of that and solutions that hunt and look for suspicious behavior on the business network.
- Respond: Once a cybersecurity incident has been identified, this pillar governs how to react, the steps to take to recover.
- Recover: The business needs to get up and running again and this pillar guides that process. Getting back to business in a secure way is the end goal.
Protect your business
The core pillars of cybersecurity really give a great foundation on which to protect a small business. I highly encourage every reader to dive deeper into the NIST Cybersecurity Framework 2.0 as this Security Byte only touched the very top level. NIST also offers a Quick-Start Guide specifically for small businesses.
Subscribe to our monthly email newsletter to keep your small business up-to-date on all the latest cybersecurity news! For more information on protecting your small business from cyberattacks and other cybersecurity topics check out Small Business, Big Threat!
Photo credit: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.1299.pdf